Written by Chris Hatfield, IT Director (South Bend, IN)
In the digital age we live in, it’s important to recognize and understand cyber security threats. In this blog, we take another look at cyber security, and how important your role is in making sure your information stays safe.
What is a CYBER THREAT?
- Cyber threats cover a wide range of malicious activity that can occur through cyberspace. Such threats include web site defacement, espionage, theft of intellectual property, denial of service attacks, and destructive malware. (adopted by White House)
- Any malicious act that attempts to gain access to a computer network without authorization or permission from the owner
Watch a Video
MOTIVATION – What is the goal of these attacks?
- Money: Trying to make a buck.
- Information: Trying to steal valuable information and sell that information.
- Entertainment: Just for fun, or maybe the challenge.
- Disruption: Make a statement, be a nuisance, or get in the news.
IDENTIFYING TARGETS – What do we have that a hacker wants?
- Passwords
- Credit Card Numbers
- Bank Account Information
- Social Security Numbers
- Files from your computer or the network
- Your computer
Commonly Used Cyber Threats
Phishing:
The act of sending email that falsely claims to be from a legitimate organization. This is usually combined with a request for information.
How to detect a Phishing scam:
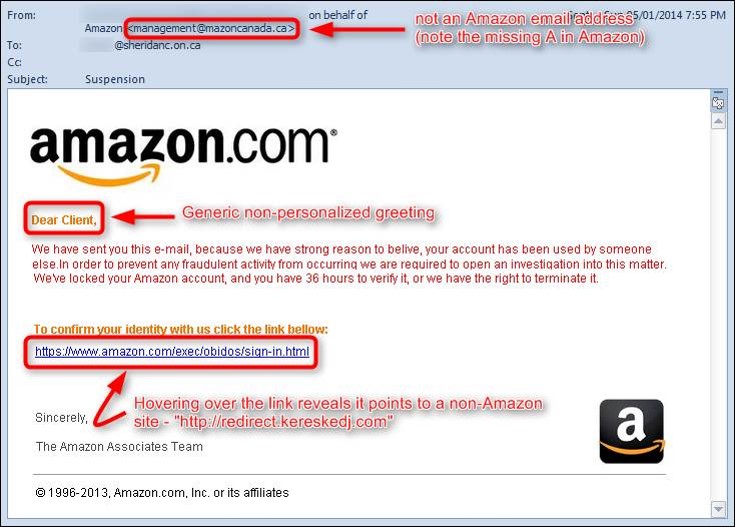
- Check the ”˜From’ address: Lazy scammers will not spoof the address.
- Look at the salutation: Is it generic?
- Examine the message: Is it a scare tactic? Is there a sense of urgency?
- Hover over links: Hovering reveals the true destination of the link.
- Check the attachment: Does the attachment end with the following:
- .EXE .BAT .PHP .SCR .ZIP
- If it does, don’t open it!
Spear Phishing:
A type of Phishing scam that TARGETS a specific individual, organization or business
What does Spear Phishing look like:
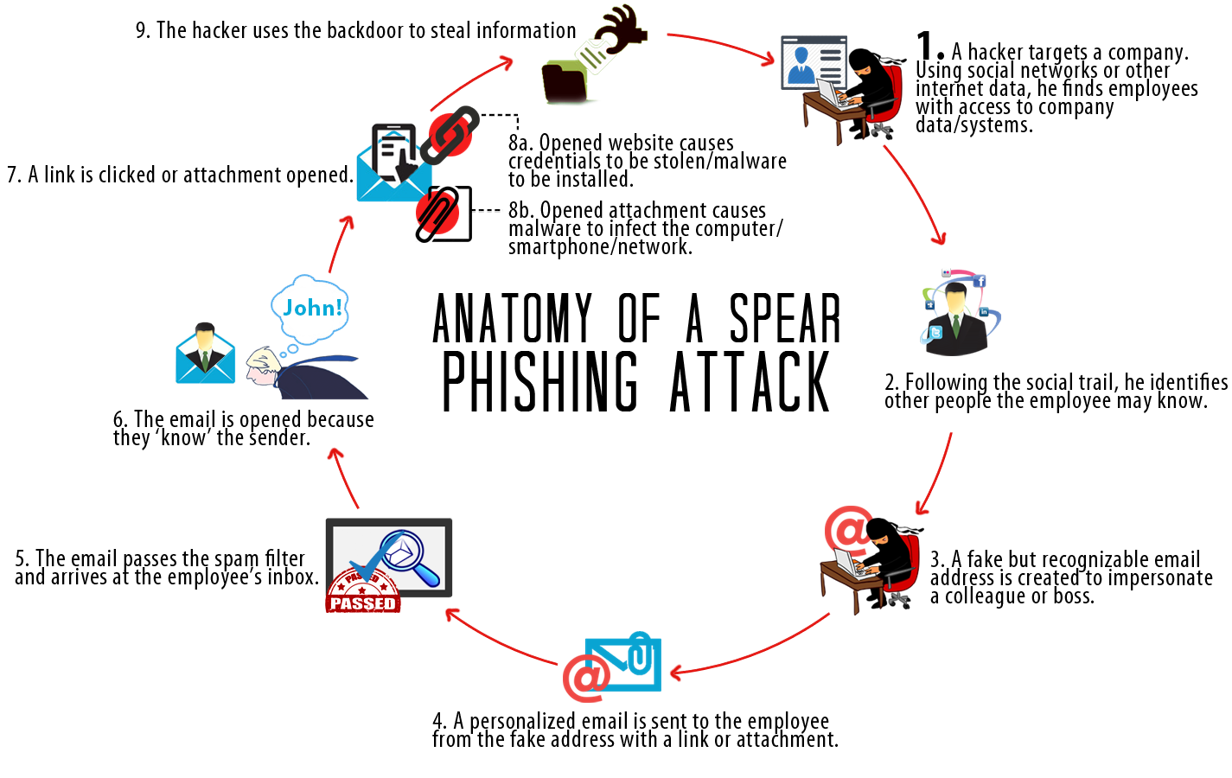
Spear Phishing – The Why
- Higher probability of success
- More time invested in researching target.
- Customized phishing email has better chance of success.
- Higher chances of substantial reward
- The installation of ”˜Ransomware’.
- Possibility of CEO fraud, such as wire transfers.
Spear Phishing – How to avoid
- Ask yourself the following:
- Am I expecting a package?
- Why would {co-worker} need this wire transfer?
- Would my friend really send this email?
- Be suspicious of any attachments:
- This includes Word/Excel/PDF attachments.
Drive-by Attack:
This attack targets a person through the web browser, installing malicious software by visiting a compromised website.
What happens?
- A legitimate website is hijacked and used to push malware to unsuspecting users.
- Poisoned search results behind trending news items on sites like Google and Yahoo.
- Social networks such as Facebook and Twitter are uses to load malware on computers.
Examples:
Malware
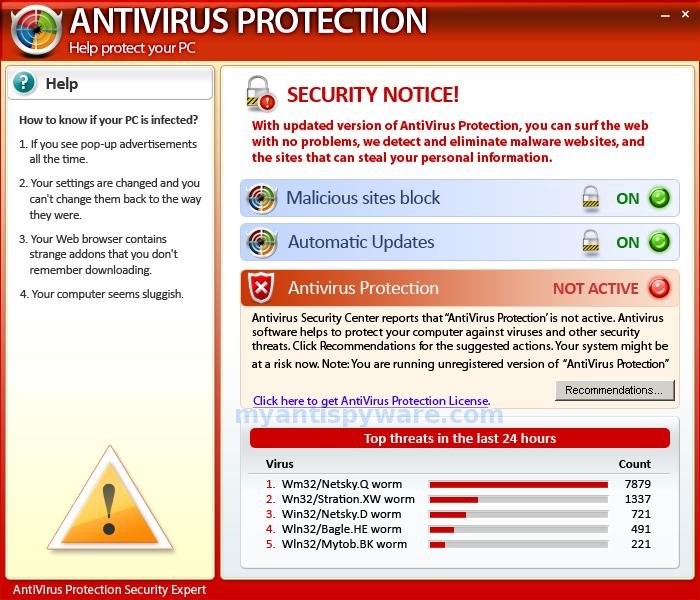
Don’t fall for this scam and download a non-existent antivirus program! Verify the anti-virus program that pops up is actually your software (Norton, TrendMicro, etc.). Be safe, don’t click a pop-up!”
BEWARE CRYPTO LOCKER!
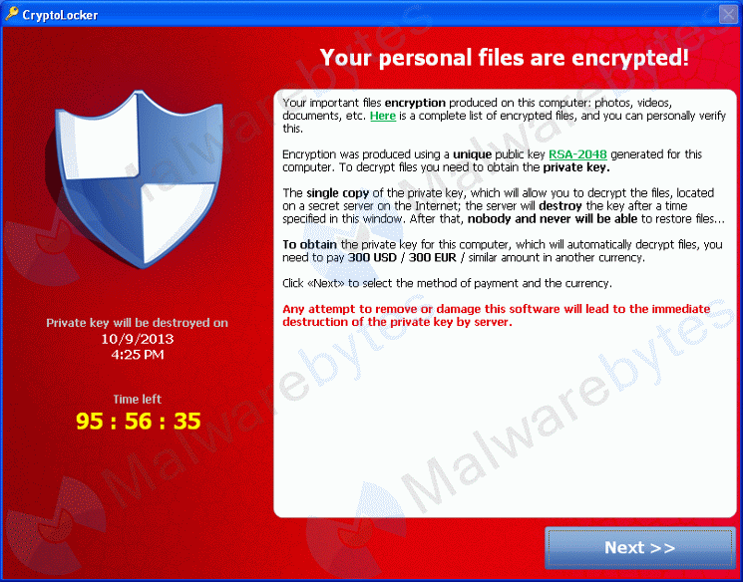
This is a global ransomware threat that has infected more than 300,000 networks in the US alone.
Vishing:
A form of Phishing using the phone (voice phishing) to persuade the end user into giving up critical or personal information.
Telephone fraud is estimated to cost companies $46 billion per year!
What are they looking for:
- Employee information.
- Social Security Numbers.
- User Credentials.
- Home addresses.
- ANY information about a company’s technology or processes.
How to protect yourself:
- No information should be given out without verifying the caller’s identity.
- Ask for the callers name.
- Ask for the company.
- Ask for the caller’s title.
- Ask for a number on which you can call them back.
Watch this video to learn more
If you don’t want to be a victim of cyber attacks, here’s one thing to keep in mind:
